1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
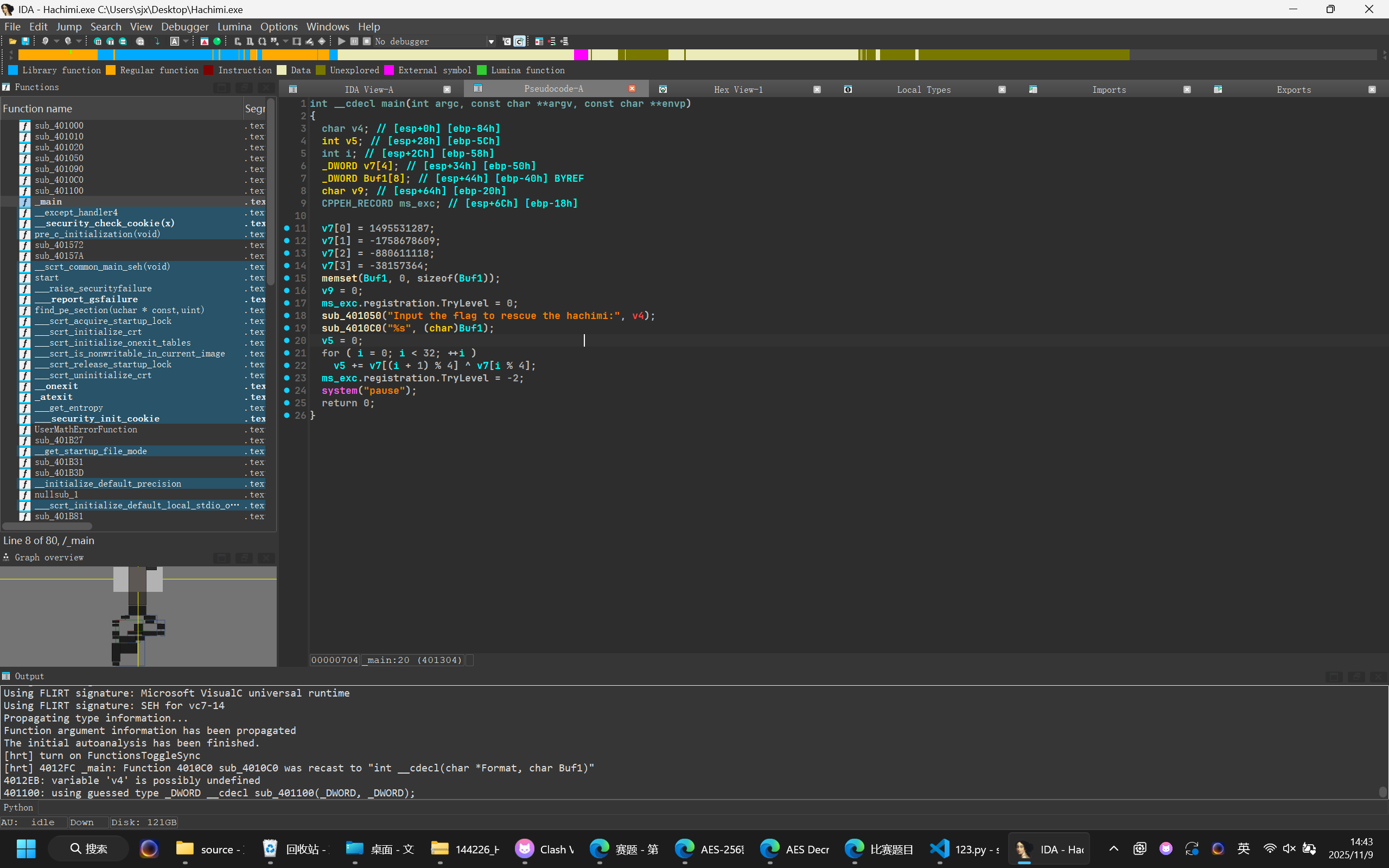
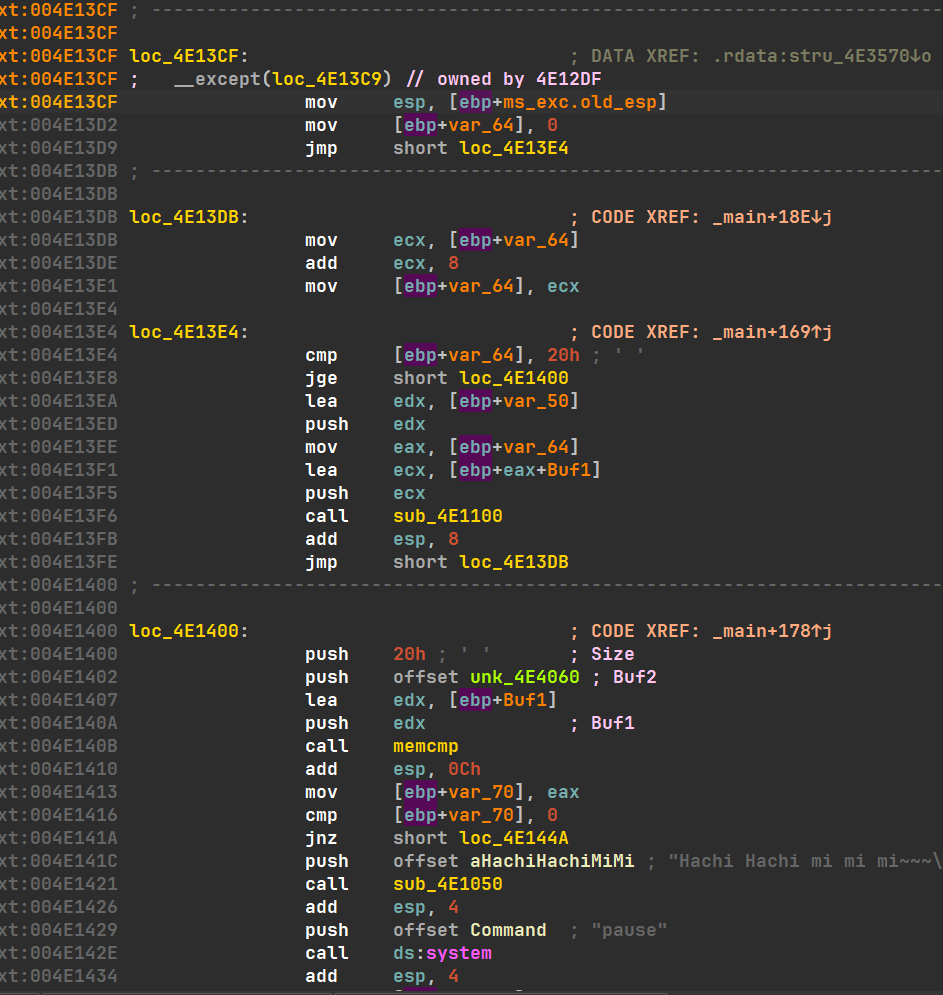
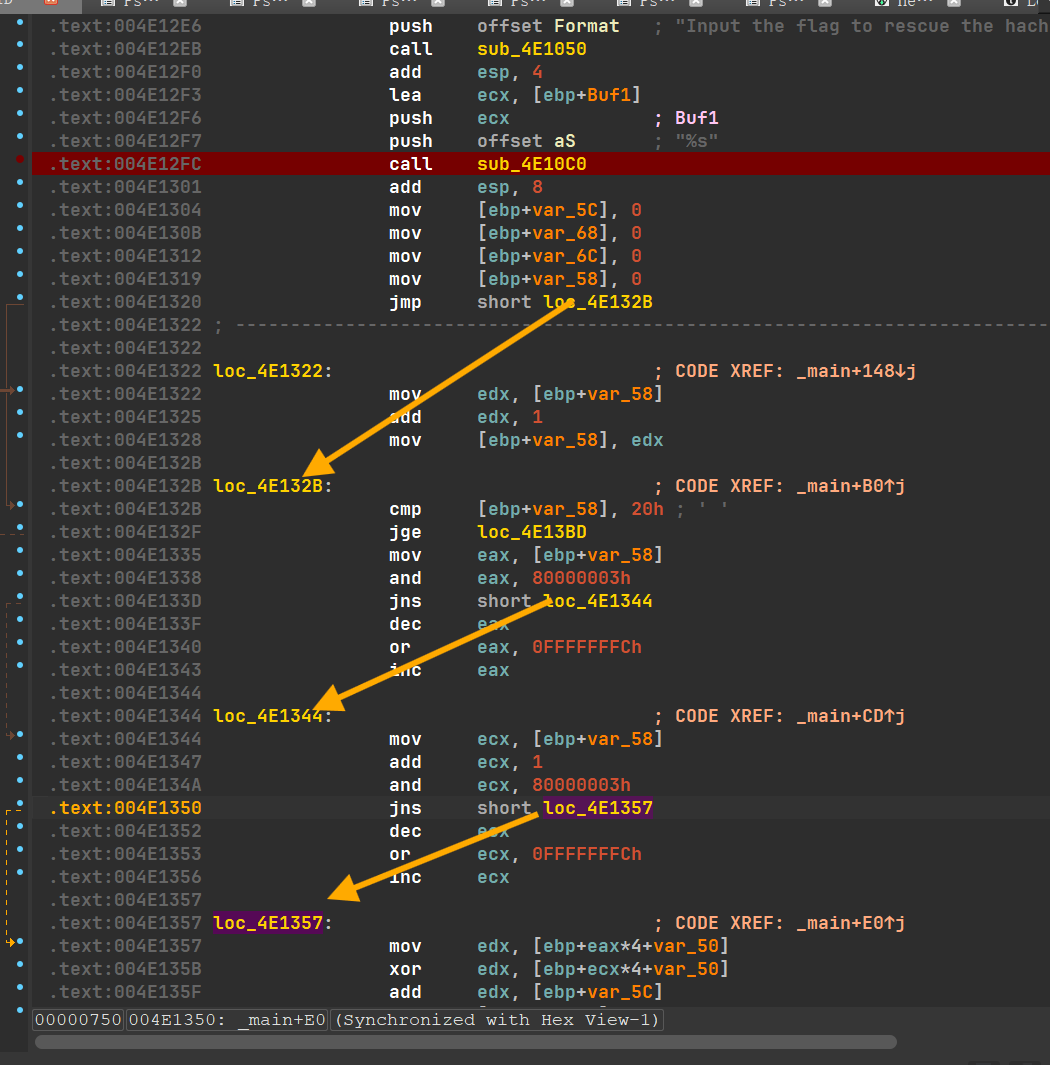
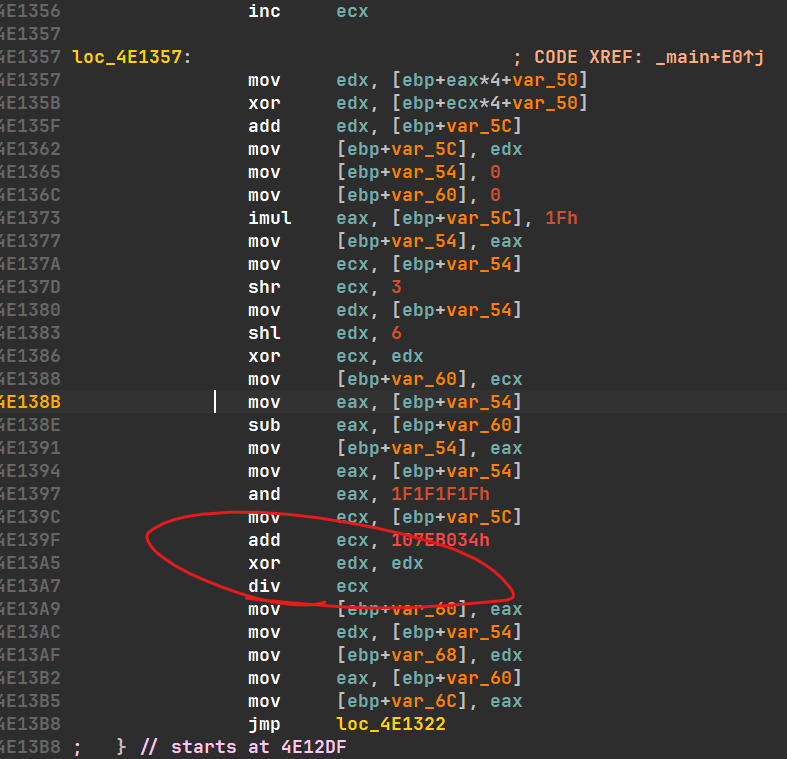
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
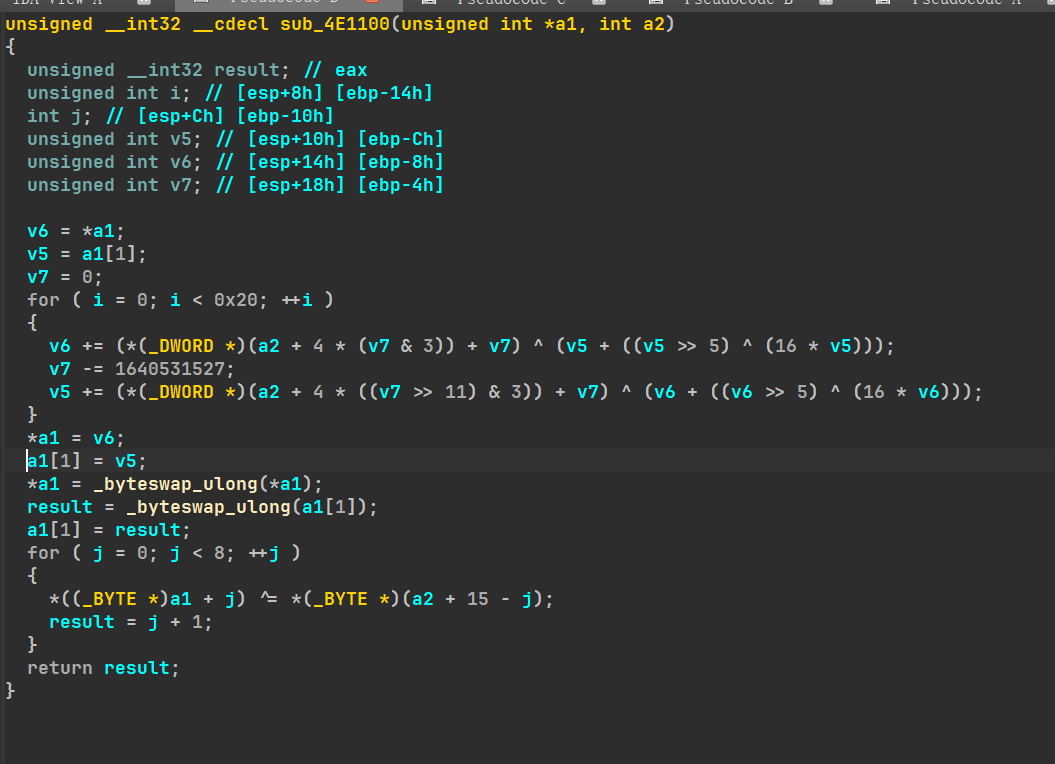
| #include<iostream>
#include<string>
#include<algorithm>
#include<vector>
#include<stdint.h>
using namespace std;
uint32_t v8[4]={};
uint8_t v9[32]={0x4D,0x7A,0x3E,0x7A,0x84,0xFF,0x51,0xB1,0x31,0x97,0xFB,0xDC,0x2B,0xA4,0xCD,0xFB,0x85,0xCD,0xA,0x2B,0xBD,0x91,0xCF,0x69,0xBA,0x2B,0x70,0xD5,0x43,0xB8,0x3E,0x1f};
unsigned long byteswap_manual(unsigned long value)
{
return ((value>>24) & 0xFF) |
((value >> 8) & 0xFF00) |
((value << 8) & 0xFF0000) |
((value << 24) & 0xff0000);
}
void tea_dec(uint32_t* a1, uint32_t* a2) {
unsigned __int32 result;
unsigned int i;
int j;
unsigned int v5 = 0;
unsigned int v6 = 0;
for ( j = 0; j < 8; ++j )
{
*((uint8_t *)a1 + j) ^= *(uint8_t *)(a2 + 15 - j);
}
*a1 = byteswap_manual(*a1);
*(a1+1) = byteswap_manual(*(a1+1));
uint32_t v0 = a1[0], v1 = a2[1];
uint32_t delta = 1640531527;
uint32_t v7 = 32 * (-delta);
for (int i = 0; i < 32; i++) {
v5 -= (*(uint32_t *)(a2 + 4 * ((v7 >> 11) & 3)) + v7) ^ (v6 + ((v6 >> 5) ^ (16 * v6)));
v7 += 1640531527;
v6 -= (*(uint32_t *)(a2 + 4 * (v7 & 3)) + v7) ^ (v5 + ((v5 >> 5) ^ (16 * v5)));
}
*(uint32_t*)(v9+j) = v0;
*(uint32_t*)(v9+j) = v1;
return ;
}
int main()
{
v8[0] = 1495531287;
v8[1] = -1758678609;
v8[2] = -880611118;
v8[3] = -38157364;
for(int j = 0;j < 8;j+=2)
tea_dec((uint32_t*)(v9+j),v8);
for(char a:v9)
cout<<a;
}
|